What We Deliver: Managed Continuous Vulnerability Scanning
Siege Cyber provides fully managed continuous vulnerability scanning across your entire infrastructure. We deploy, configure, and manage enterprise-grade scanning tools that monitor your environment 24/7, alert you immediately when critical vulnerabilities emerge, provide expert analysis to filter false positives, and deliver ongoing compliance reporting. You get always-on visibility without the overhead of managing scanning infrastructure yourself.
Here is what you get:
- 24/7 automated scanning across all infrastructure – We deploy continuous scanning across your external perimeter (internet-facing systems), internal network infrastructure, cloud environments (AWS, Azure, GCP), containers, and SaaS applications. Scans run continuously in the background, identifying new vulnerabilities within hours of CVE disclosure, detecting new systems as they come online, and flagging configuration drift that introduces risk.
- Real-time alerting for critical and high-risk vulnerabilities – When a critical vulnerability is discovered in your environment (either through new CVE disclosure or newly detected exposure), you receive immediate notification. We filter out the noise and alert you only to findings that genuinely require urgent attention. No more waiting weeks or months to discover you are running vulnerable software that attackers are actively exploiting.
- Expert analysis and false positive filtering – Continuous scanning generates significant volume. Not all findings are genuine vulnerabilities, and not all vulnerabilities pose equal risk. We provide expert analysis to confirm genuine security issues, filter false positives, prioritise findings based on exploitability and business impact, and provide clear remediation guidance. You get intelligence, not just alerts.
- Automated compliance evidence for auditors – Continuous scanning provides the documented evidence auditors expect for ISO 27001 Annex A.12.6.1 (management of technical vulnerabilities), SOC 2 CC7.1 (system monitoring), and Essential Eight vulnerability management requirements. We deliver compliance-ready reports showing that you maintain ongoing visibility into your security posture, not just periodic snapshots.
- Integration with compliance automation platforms – If you are using Vanta or Drata for ISO 27001 or SOC 2 compliance, we integrate continuous scanning directly into your compliance workflow. Vulnerability data feeds automatically into your compliance platform, control evidence is collected continuously, and audit reports are generated on demand. No manual data collection required.
- Trend analysis and security posture metrics – Beyond identifying individual vulnerabilities, continuous scanning reveals patterns. Are new vulnerabilities appearing faster than you are remediating them? Which systems or departments consistently expose risk? Is your overall security posture improving or degrading over time? We provide executive dashboards and trend analysis that answers these strategic questions.
- Ongoing remediation support and guidance – When vulnerabilities are identified, we provide detailed remediation guidance including specific patch versions, configuration changes, mitigation strategies for vulnerabilities that cannot be immediately patched, and risk acceptance documentation for findings you choose not to remediate. We help you prioritise what to fix first based on actual risk, not just CVSS scores.
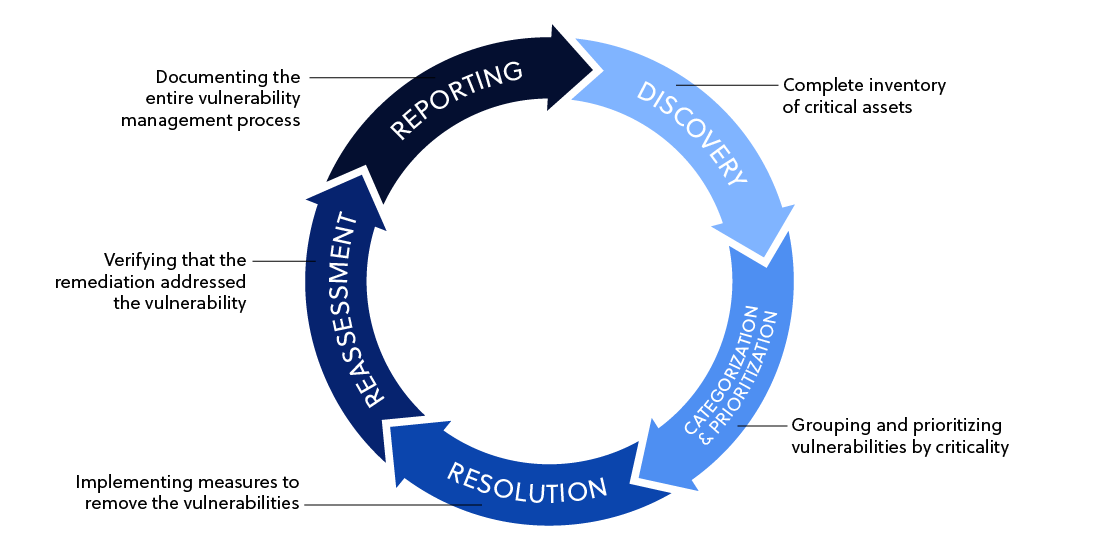
Our Continuous Vulnerability Scanning Process
We have deployed continuous scanning for dozens of Australian organisations. Here is how it works.
1. Scoping and Infrastructure Discovery
We meet with your team to understand your environment: cloud infrastructure, on-premises systems, SaaS applications, development environments, and compliance requirements. We conduct automated discovery to map your external attack surface, identify all assets requiring monitoring, and determine appropriate scanning frequency and scope. You get a clear picture of what will be monitored and how.
2. Scanner Deployment and Configuration
We deploy and configure enterprise-grade continuous scanning tools across your environment. For cloud infrastructure, this typically involves read-only API access. For internal networks, we deploy scanning appliances or agents. For external perimeter monitoring, we configure authenticated and unauthenticated scanning. All scanning is configured to run continuously without requiring manual intervention or disrupting operations.
3. Baseline Scan and Initial Vulnerability Assessment
We conduct an initial comprehensive scan to establish your baseline security posture. This identifies existing vulnerabilities before continuous monitoring begins. We deliver a prioritised report of current findings, remediation guidance for critical and high-risk issues, and a remediation roadmap. This baseline becomes the starting point for measuring improvement over time.
4. Continuous Monitoring and Real-Time Alerting (Ongoing)
Once baseline remediation is underway, continuous scanning begins. Your environment is monitored 24/7 for new vulnerabilities, configuration changes, newly deployed systems, and emerging threats. Critical findings trigger immediate alerts. High and medium-risk findings are batched into regular reports (daily or weekly, depending on your preference). You maintain ongoing visibility without gaps between scans.
5. Expert Analysis and Remediation Guidance (Ongoing)
Our security team reviews all findings to confirm genuine vulnerabilities, filter false positives, assess business impact, and provide remediation guidance. You are not left alone with raw scanner output. You get expert analysis that explains what each finding means for your environment, how urgent remediation is, and what to do about it.
6. Monthly Compliance Reporting and Executive Dashboards (Monthly)
Every month, we deliver comprehensive reports showing overall security posture, new vulnerabilities discovered, vulnerabilities remediated, outstanding findings by severity, trend analysis over time, and compliance evidence formatted for auditors. Executive dashboards provide business-level metrics that leadership and boards can understand without diving into technical detail.
Who This Is For: Managed Vulnerability Scanning Services Australia
This service is designed for Australian SaaS companies, technology businesses, financial services organisations, healthcare providers, and any business that operates dynamic infrastructure where quarterly scanning leaves dangerous exposure gaps.
You are a good fit if:
- You need to satisfy Essential Eight weekly vulnerability scanning requirements and want continuous coverage that exceeds minimum maturity levels
- You are pursuing or maintaining ISO 27001 or SOC 2 compliance and auditors expect evidence of continuous vulnerability management
- You operate cloud-native or DevOps environments where infrastructure changes daily and periodic scanning cannot keep pace
- You have experienced a breach or near-miss caused by a vulnerability that appeared between scheduled scans
- Your board, investors, or customers are asking how you maintain continuous visibility into security vulnerabilities
- You run mission-critical systems where even short exposure windows are unacceptable
- You do not have internal resources to deploy, manage, and monitor vulnerability scanning tools 24/7
- You want to demonstrate security maturity beyond basic compliance checkboxes
If you are using Vanta or Drata for compliance automation, continuous vulnerability scanning integrates directly with these platforms. As official partners of both Vanta and Drata, we configure scanning tools that feed vulnerability data automatically into your compliance dashboard, provide the evidence auditors expect for ISO 27001 and SOC 2, and eliminate manual evidence collection. The platforms automate compliance tracking while we provide the expert security analysis these tools cannot deliver.

Why Choose Siege Cyber for Vulnerability Management Services
20+ years of offensive security and vulnerability research experience. Our Technical Director, Peter Stewart, has spent over two decades breaking into systems and identifying vulnerabilities. We know which findings actually matter, which are false positives, and what attackers would exploit first. You get expert analysis, not just automated scanner output.
We understand Australian compliance requirements. Essential Eight requires weekly vulnerability scanning at minimum (continuous exceeds this requirement). ISO 27001 Annex A.12.6.1 requires management of technical vulnerabilities with ongoing monitoring. SOC 2 CC7.1 requires system monitoring for security events. APRA CPS 234 expects financial institutions to maintain continuous information security capability. We deliver scanning that satisfies all these frameworks simultaneously.
Fully managed service, not just tool licensing. Many vendors sell you a vulnerability scanner and leave you to figure out deployment, configuration, alert tuning, false positive filtering, and remediation prioritisation. We handle everything: scanner deployment, ongoing management, expert analysis, remediation guidance, and compliance reporting. You get outcomes, not homework.
Official Vanta and Drata partner for compliance integration. We know exactly how to configure continuous scanning for ISO 27001 and SOC 2 compliance within these platforms. Vulnerability data feeds automatically into your compliance dashboard, control evidence is collected continuously, and audit reports are generated on demand. If you are using compliance automation, we make it actually work.
Real-time alerting with intelligent filtering. Continuous scanning generates thousands of findings. Most are low-risk or false positives. We filter the noise and alert you immediately to critical findings that require urgent attention, while batching lower-priority findings into regular reports. You get actionable intelligence, not alert fatigue.
Frequently Asked Questions
What is the difference between continuous vulnerability scanning and periodic vulnerability assessment?
Periodic vulnerability assessment runs scheduled scans (monthly, quarterly, annually) and provides a point-in-time snapshot of your security posture. Continuous vulnerability scanning monitors your environment 24/7, identifying new vulnerabilities within hours of CVE disclosure and detecting new systems or configuration changes immediately. The key difference is the exposure gap: periodic scanning leaves you blind to what happens between scans, while continuous scanning maintains always-on visibility. In 2024 alone, over 52,000 new CVEs were disclosed. Waiting months between scans means missing critical vulnerabilities that attackers exploit within hours.
Will continuous scanning disrupt our operations or slow down systems?
Modern continuous scanning is designed to be non-disruptive. Scans run in the background with throttled traffic to avoid overwhelming systems. For cloud infrastructure, we use read-only API access that does not affect performance. For internal networks, scanning is distributed over time and throttled to prevent network congestion. That said, we always coordinate scan timing with your team and can adjust scan intensity if needed. Most clients never notice scanning is happening.
How quickly will we be alerted to critical vulnerabilities?
For critical vulnerabilities (such as remotely exploitable flaws with active exploitation in the wild), you receive alerts within hours of discovery. For example, if a new critical CVE is published affecting software in your environment, our continuous scanning detects it and notifies you the same day. For high-risk findings, alerts are typically batched into daily or weekly reports depending on your preference. You define the alert thresholds during initial setup.
Do we still need annual penetration testing if we have continuous vulnerability scanning?
Yes. Continuous vulnerability scanning and penetration testing serve different purposes. Scanning identifies known vulnerabilities, missing patches, and misconfigurations using automated tools. Penetration testing involves manual exploitation by experienced security professionals to find complex vulnerabilities, business logic flaws, and chained attack paths that scanners cannot detect. Both are valuable, and most compliance frameworks (ISO 27001, SOC 2, Essential Eight) require both continuous vulnerability management and periodic penetration testing.
How does continuous scanning help with ISO 27001 and SOC 2 compliance?
ISO 27001 Annex A.12.6.1 requires organisations to obtain timely information about technical vulnerabilities and take appropriate measures. Continuous scanning provides documented evidence that you maintain ongoing awareness of vulnerabilities, not just periodic snapshots. SOC 2 Trust Service Criteria CC7.1 requires the entity to monitor system components and protect against threats. Continuous scanning provides the system monitoring evidence auditors expect. We deliver compliance-ready reports formatted for audit that demonstrate continuous vulnerability management.
What happens if you find critical vulnerabilities in production systems?
If we identify critical vulnerabilities in production systems (particularly those with active exploitation or remote code execution capabilities), we notify you immediately via phone or secure communication channel. We provide emergency remediation guidance including available patches, workarounds if patches are not immediately available, and risk mitigation strategies. For truly critical findings affecting internet-facing systems, we treat it as a security incident requiring urgent response.
Ready to Close Your Security Exposure Gaps?
Quarterly vulnerability scans were fine five years ago. They are not sufficient in the world of AI. New vulnerabilities are disclosed daily, infrastructure changes constantly, and attackers move faster than ever. Continuous vulnerability scanning provides the always-on visibility you need to maintain security between audits, satisfy compliance requirements, and actually protect your environment rather than just checking boxes.
Book a free 30-minute consultation with our team. We will assess your infrastructure, discuss your compliance requirements, and explain exactly how continuous scanning would work for your environment. You will leave the call knowing what vulnerabilities exist right now, what ongoing visibility would look like, and how continuous scanning integrates with your existing security programme.