What We Deliver: A Realistic Incident Response Test
When you engage Siege Cyber for a cyber tabletop exercise, you receive a complete, facilitated simulation designed specifically for your organisation and risk profile.
Customised Incident Scenario
We develop a realistic cyber incident scenario based on actual threats affecting Australian businesses in your industry. Ransomware. Data breach. Business email compromise. Supply chain attack. Whatever keeps you up at night, we'll simulate it. The scenario includes technical details, timeline progression, stakeholder pressure, and decision points that mirror real incidents.
Professional Facilitation
Our team runs the exercise from start to finish. We present the scenario, introduce new information as the incident evolves, challenge assumptions, ask hard questions, and keep the exercise moving. You're not reading from a script—we're simulating the chaos and pressure of an actual incident.
Multi-Level Participation
We design exercises that involve both your technical team (IT managers, security staff) and business leadership (executives, board members, legal, communications). Everyone understands their role, tests their decision-making, and learns how to work together during a crisis.
Gap Identification and Documentation
Throughout the exercise, we document what works and what doesn't. Unclear responsibilities. Missing procedures. Communication breakdowns. Technical gaps. Compliance obligations nobody understood. You'll receive a detailed findings report showing exactly what needs to be fixed.
Actionable Remediation Recommendations
We don't just identify problems—we tell you how to fix them. Update your incident response plan here. Add this communication template. Clarify this decision authority. Implement this technical control. Every finding comes with a practical recommendation.
Compliance Evidence Package
ISO 27001 auditors want to see evidence of incident response testing. We provide documentation proving you've conducted a tabletop exercise, including participant lists, scenario details, findings, and remediation plans. Everything auditors and insurers expect to see.
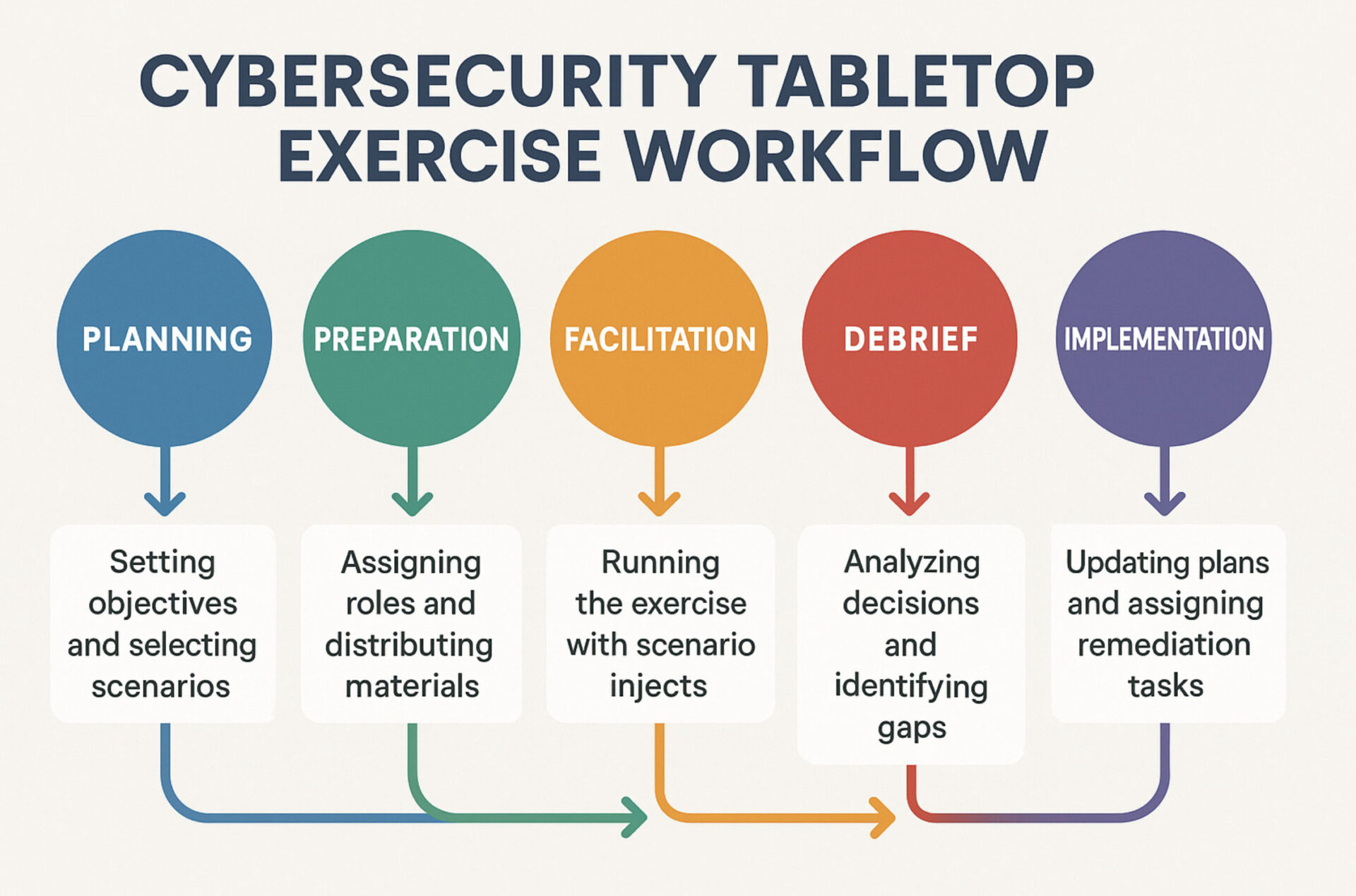
Our Cybersecurity Tabletop Exercise Process
Step 1: Scoping and Scenario Design
We start with a consultation to understand your organisation, technology environment, existing incident response plan, and biggest concerns. What scenarios are most relevant to your business? Who needs to participate? What compliance requirements are you satisfying? We design the exercise around your actual risks and objectives.
Step 2: Participant Preparation
We provide pre-exercise materials to participants so they know what to expect. Background on the scenario type, their role during the exercise, and any documentation they should review beforehand (your incident response plan, contact lists, communication templates). We want participants prepared, not ambushed.
Step 3: Tabletop Exercise Facilitation
We run the exercise as a facilitated workshop, typically 3-4 hours. We introduce the initial scenario, then progressively reveal new information as the "incident" evolves. Participants discuss their response, make decisions, and work through procedures. We challenge assumptions, probe decision-making, and identify gaps in real-time. The session is collaborative, not confrontational—we're building capability, not assigning blame.
Step 4: Immediate Debrief
At the end of the exercise, we facilitate an immediate debrief discussion. What went well? What was confusing? What surprised participants? What would they do differently? We capture lessons learned while they're fresh and document areas requiring improvement.
Step 5: Findings Report and Recommendations
Within one week of the exercise, we deliver a detailed findings report. We document every gap identified, provide context on why it matters, and offer specific remediation recommendations. The report includes compliance evidence for ISO 27001 auditors and cyber insurance applications.
Step 6: Remediation Support (Ongoing)
We help you implement the findings. Update your incident response plan. Develop missing procedures. Clarify roles and responsibilities. Many clients engage our vCISO service to maintain incident response capability over time, including annual tabletop exercises to ensure continuous readiness.
Who Cyber Tabletop Exercises Are For
Organisations with Existing Incident Response Plans
You've documented your incident response procedures, but you've never tested whether they actually work. A tabletop exercise reveals gaps before you're forced to use the plan during a real incident. We validate your plan against realistic scenarios and identify what needs improvement.
Businesses Pursuing ISO 27001 Certification
ISO 27001 Annex A.16.1.5 requires periodic testing of incident response plans. Auditors expect to see evidence that you've actually tested your capability, not just documented procedures. Our tabletop exercises satisfy ISO 27001 testing requirements and provide the compliance evidence auditors expect.
Essential Eight Implementation Projects
The Essential Eight guidance recommends testing incident response capability as part of a mature security program. If you're implementing Essential Eight for government contracts or internal security maturity, tabletop exercises demonstrate that you can actually respond to incidents, not just prevent them.
Organisations Applying for Cyber Insurance
Cyber insurance applications increasingly ask about incident response testing. Do you conduct regular exercises? How recently? What scenarios have you tested? Running annual tabletop exercises demonstrates incident preparedness to insurers and may improve your premiums.
Executive Teams and Boards
Board members and executives need to understand their role during cyber incidents. Who authorises spending? Who communicates with customers? Who engages legal counsel? Tabletop exercises designed for leadership build decision-making confidence and clarify responsibilities before crisis hits.
Businesses After Recent Incidents
You've experienced a cyber incident and learned hard lessons. A post-incident tabletop exercise tests your updated procedures, ensures the organisation has learned from the experience, and validates that you're better prepared for the next incident.
Merger and Acquisition Due Diligence
Acquiring companies want to understand cyber risk. Selling companies want to demonstrate security maturity. A recent tabletop exercise proves incident response capability and provides evidence for due diligence processes.

Why Work with Siege Cyber for Tabletop Exercises
We've Responded to Real Australian Incidents
Our facilitators have guided Australian businesses through actual ransomware attacks, data breaches, and business email compromise incidents. We don't simulate theoretical scenarios from overseas—we design exercises based on real incidents affecting Australian organisations, with realistic technical details and business context.
We Understand Australian Compliance Requirements
Privacy Act notification obligations. OAIC reporting. ACSC voluntary disclosure. Mandatory ransomware reporting under the Cyber Security Act 2024. APRA CPS 234 for financial services. We build scenarios that test your understanding of Australian regulatory requirements, not just technical response.
Multi-Level Exercise Design
Many tabletop exercises focus only on technical teams or only on executives. We design exercises that involve both layers, testing technical response capability and business decision-making simultaneously. Your IT manager and your CEO both participate, both learn, and both understand each other's constraints.
Realistic Scenarios with Technical Depth
We're not just reading hypothetical scenarios from a template. Our team includes penetration testers and incident responders who understand how attacks actually unfold. We simulate realistic technical details, attack progression, and decision points based on genuine threat actor behaviour.
Actionable Findings, Not Just Observations
Some facilitators identify gaps and walk away. We provide specific remediation recommendations for every finding. Update this procedure. Add this communication template. Clarify this authority. Implement this technical control. You leave the exercise knowing exactly what to fix and how to fix it.
Fixed Pricing with No Hidden Costs
After the scoping discussion, we provide a fixed price for the complete exercise—scenario development, facilitation, findings report, and compliance documentation. You know exactly what the investment is before committing. No hourly billing, no scope creep.
Frequently Asked Questions
How long does a tabletop exercise take?
Most exercises run 3-4 hours, including scenario presentation, team discussion, decision-making simulation, and immediate debrief. We can design shorter 2-hour exercises for specific scenarios or extended half-day sessions for complex multi-scenario exercises. The optimal length depends on your objectives and participant availability.
Who should participate in the exercise?
It depends on what you're testing. Technical exercises involve IT managers, security staff, and system administrators. Business continuity exercises include executives, legal, communications, and operations leaders. We recommend multi-level exercises involving both technical and business participants, as real incidents require coordination across the entire organisation.
How is a tabletop exercise different from penetration testing?
Penetration testing assesses your technical security controls by simulating an attack against your systems. Tabletop exercises test your people, processes, and decision-making by simulating an incident scenario. Both are valuable, but they test different aspects of your security posture. Many organisations do both annually.
Do you need access to our systems to run the exercise?
No. Tabletop exercises are discussion-based simulations, not technical attacks. We don't touch your production systems. We present hypothetical scenarios and your team discusses their response. It's completely safe and causes no disruption to your operations.
Can we use ACSC's free Exercise in a Box instead?
ACSC's Exercise in a Box is an excellent free resource providing scenario templates and facilitation guidance. However, it requires internal facilitation, scenario customisation, and expertise to run effectively. Many organisations find professional facilitation more effective because we bring external perspective, realistic scenarios based on current threats, and experience identifying gaps organisations miss internally.
How often should we conduct tabletop exercises?
ISO 27001 requires periodic testing—most organisations interpret this as annual. The Australian Government ISM recommends annual exercise of cyber incident response plans. We suggest annual exercises as a baseline, with additional exercises after significant changes (new systems, organisational restructuring, major incidents in your industry).
What happens if the exercise reveals major gaps in our plan?
That's exactly why you conduct exercises—to find gaps in a safe environment rather than during a real incident. We document every finding and provide remediation recommendations. Many clients engage us to help implement the fixes, whether through plan updates, procedure development, or ongoing vCISO support.
Can you run exercises for specific compliance frameworks?
Yes. We design exercises aligned with ISO 27001 testing requirements, Essential Eight implementation, APRA CPS 234 for financial services, or general incident response capability. Tell us your compliance objectives during scoping and we'll ensure the exercise satisfies those requirements while providing genuine learning value.
Test Your Incident Response Before You Need It
Every organisation hopes they'll never face a cyber incident. Smart organisations prepare anyway.
Siege Cyber has facilitated tabletop exercises for Australian SaaS companies, financial services firms, healthcare providers, and SMBs across every sector. We've helped organisations satisfy ISO 27001 testing requirements, prepare boards for crisis decision-making, and identify critical gaps before they become real problems.
Book a free consultation to discuss a tabletop exercise for your organisation. We'll understand your objectives, explain our approach, and provide a clear proposal with scenario options and fixed pricing. No obligation, no pressure—just honest advice about testing your incident response capability.