What We Deliver
Siege Cyber provides comprehensive red team testing that simulates real-world adversary tactics, techniques, and procedures (TTPs) based on the MITRE ATT&CK framework. We combine technical exploitation, social engineering, and assume-breach scenarios to achieve defined objectives while your security team attempts to detect and respond. You get an honest assessment of how your organisation would fare against a determined attacker.
Here is what you get:
- Objective-based adversary simulation – Unlike traditional penetration testing that aims to find as many vulnerabilities as possible, red team engagements focus on achieving specific objectives (accessing sensitive data, compromising critical systems, exfiltrating intellectual property). We use whatever techniques are necessary to reach the goal while remaining undetected, just like a real attacker would.
- Multi-vector attack scenarios – We employ a combination of technical exploitation (network, web application, cloud infrastructure), social engineering (phishing, pretexting, phone-based attacks), and assume-breach scenarios (simulating an attacker who has already gained initial access). This tests your defences comprehensively rather than focusing on a single attack surface.
- MITRE ATT&CK-aligned tactics and techniques – Our red team operations follow the MITRE ATT&CK framework, using documented adversary tactics and techniques observed in real-world breaches. This ensures the simulation reflects how actual threat actors operate, not just theoretical attack scenarios.
- Detection and response testing – Throughout the engagement, we document every action we take, every system we compromise, and every alarm we trigger (or do not trigger). This shows exactly what your security operations centre detected, how quickly they responded, and where critical gaps exist in your monitoring and alerting.
- Stealth and persistence simulation – We operate covertly over an extended period (typically 2-6 weeks) to simulate a determined attacker who is trying to avoid detection. This tests whether your security team can identify low-and-slow attacks, lateral movement, privilege escalation, and data staging before exfiltration occurs.
- Comprehensive debrief and remediation roadmap – After the engagement, we conduct a detailed debrief with your security team, walking through every stage of the attack, explaining how we bypassed controls, and identifying where detection failed. You receive a prioritised remediation roadmap that addresses people, process, and technology gaps.
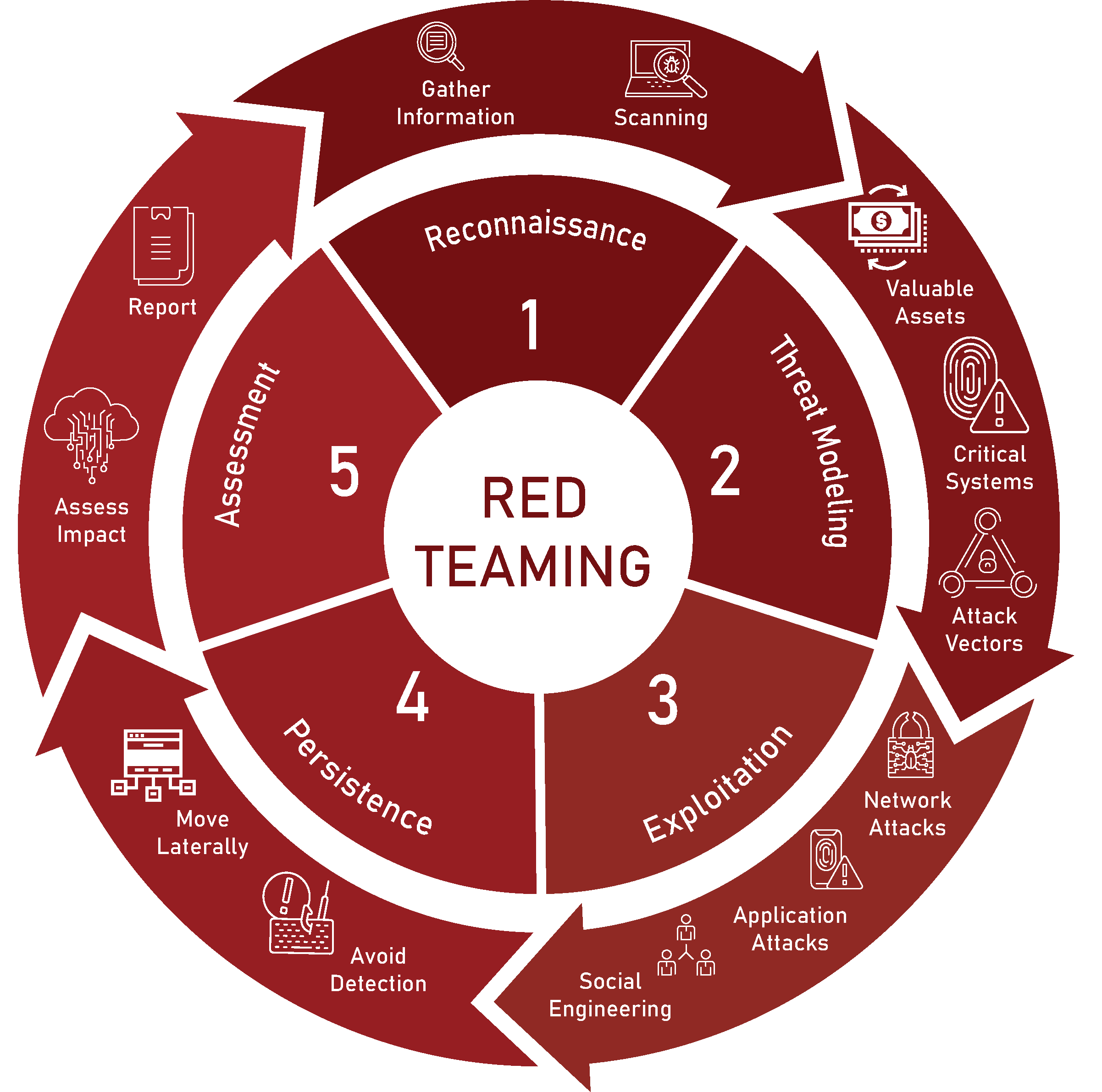
Our Red Team Assessment Process
We have conducted red team engagements for some of Australia's most security-conscious organisations. Here is how it works.
1. Scoping and Objective Definition
We meet with your leadership team to define the red team objectives. What are we trying to access or compromise? What tactics are in scope (technical only, or including social engineering)? Who knows about the exercise (typically only senior leadership), and who will be tested (your security operations team)? We also establish rules of engagement, escalation procedures, and success criteria.
2. Reconnaissance and Target Identification
We conduct extensive reconnaissance using open-source intelligence (OSINT), social media analysis, employee enumeration, infrastructure mapping, and third-party exposure analysis. This mirrors how a real attacker would research your organisation before launching an attack. We identify potential entry points, key targets, and attack vectors that align with the engagement objectives.
3. Initial Access and Foothold Establishment
We attempt to gain initial access to your environment using techniques appropriate to the engagement scope. This might include spear-phishing campaigns targeting specific employees, exploiting vulnerabilities in external infrastructure, compromising third-party services, or assume-breach scenarios where we simulate an attacker who has already bypassed perimeter defences. The goal is to establish a persistent foothold without triggering detection.
4. Lateral Movement and Privilege Escalation
Once inside, we move laterally through your network to escalate privileges, compromise additional systems, and work toward the engagement objectives. This phase tests your network segmentation, privileged access controls, endpoint detection capabilities, and security monitoring effectiveness. We document every system accessed, every credential harvested, and every defensive control encountered.
5. Objective Achievement and Persistence
We work toward achieving the defined objectives (accessing sensitive data repositories, compromising critical systems, demonstrating potential for data exfiltration) while maintaining persistence in your environment. Throughout this phase, we are simulating what an advanced persistent threat would do once they have achieved their goals: establishing multiple backdoors, maintaining long-term access, and covering tracks.
6. Detection Testing and Blue Team Engagement (Throughout)
If your security operations team detects our activity and initiates incident response, we document their response time, effectiveness, and completeness. Did they identify the full scope of the compromise, or only the surface activity? This purple team element (red team working with blue team after detection) provides valuable learning for your security operations.
7. Comprehensive Debrief and Reporting
We deliver a detailed red team report that includes an executive summary (for leadership), a complete attack narrative (documenting every step taken), a detection and response analysis (what was detected and when), and a prioritised remediation roadmap. We also conduct an in-depth debrief session with your security team, walking through the attack chain and explaining how each technique worked.
Who This Is For
Red team testing is designed for organisations with mature security programmes that need to validate their detection and response capabilities under realistic conditions. This service is not suitable for organisations that have never had a penetration test or vulnerability assessment. You need a solid security foundation before red teaming makes sense.
You are a good fit if:
- You have an established security operations capability (in-house SOC or outsourced managed detection and response) and want to test its effectiveness
- You have completed multiple rounds of penetration testing and vulnerability assessments and are confident in your technical controls
- Your board, executives, or regulators are asking how you would respond to a sophisticated, multi-stage attack
- You operate in a high-risk industry (financial services, healthcare, critical infrastructure) and need assurance that your defences would hold up against advanced threats
- You have recently invested significantly in security tooling (SIEM, EDR, NDR, SOAR) and want to validate your return on investment
- You are preparing for regulatory assessments that require demonstration of incident detection and response capabilities (APRA CPS 234 for financial institutions)
- You want to identify gaps in your security operations, incident response procedures, and threat detection capabilities before an actual breach occurs
Red team testing is not appropriate for: organisations without established security operations, companies conducting their first security assessment, or businesses that do not have resources to act on findings. If you are still building foundational security controls, start with vulnerability assessment and penetration testing. Red teaming comes later, once your baseline security is solid.

Why Choose Siege Cyber
20+ years of offensive security expertise. Our Technical Director, Peter Stewart, has spent over two decades in hands-on cybersecurity roles, including penetration testing, network security engineering, and adversary simulation. We understand how attackers think, how they operate, and what techniques actually work in real-world environments.
MITRE ATT&CK-aligned methodology. We base our red team operations on the MITRE ATT&CK framework, using documented tactics and techniques observed in real adversary campaigns. This ensures the simulation reflects genuine threats your organisation might face, not just theoretical scenarios or outdated attack methods.
We test the full picture: people, process, and technology. Red teaming is not just about exploiting technical vulnerabilities. We test your security awareness (will employees click a phishing link?), your incident response procedures (does your playbook actually work?), and your detection capabilities (can your SOC identify sophisticated attacks?). You get a holistic assessment of your security programme.
Clear, actionable intelligence for multiple audiences. Our reports are written for three audiences: executives who need to understand business risk, security operations teams who need to improve detection capabilities, and technical staff who need to remediate specific vulnerabilities. Everyone gets the information they need in language they understand.
We understand Australian security requirements. For organisations in regulated industries, we know how red team testing supports compliance with APRA CPS 234 (financial services), the Privacy Act 1988 (data protection), and Essential Eight maturity assessments (government and critical infrastructure). We can align red team objectives with your specific regulatory obligations.
Frequently Asked Questions
What is the difference between penetration testing and red team testing?
Penetration testing focuses on identifying as many vulnerabilities as possible across specific systems or applications within a defined timeframe (typically 1-4 weeks). The security team usually knows it is happening. Red team testing focuses on achieving specific objectives (like accessing sensitive data) using any techniques necessary while remaining undetected for an extended period (typically 4-8 weeks). The security operations team usually does not know it is happening until they detect it. Penetration testing finds weaknesses. Red teaming tests whether you can detect and respond to attacks exploiting those weaknesses.
How long does a red team engagement take?
Most red team engagements run for 4-8 weeks, depending on the scope and objectives. This extended timeline allows us to simulate realistic attacker behaviour, including reconnaissance, initial access attempts, lateral movement, and persistence. Unlike penetration testing which happens in compressed timeframes, red teaming needs time to operate covertly and test whether your security operations can detect low-and-slow attacks.
Will our security team know the red team exercise is happening?
This depends on the engagement objectives and your organisation's preferences. In most cases, only senior leadership and key stakeholders know about the exercise beforehand. Your security operations team, incident response team, and general IT staff do not know, because we are testing their ability to detect and respond to an attack they do not expect. After detection or at the end of the engagement, we conduct a full debrief with the entire security team.
What happens if the red team gains access to sensitive data?
We treat all data encountered during testing with strict confidentiality. If we achieve the objective of accessing sensitive systems or data repositories, we document proof of access without exfiltrating actual data or causing business disruption. The goal is to demonstrate what an attacker could access, not to actually steal or manipulate information. All findings are reported only to authorised stakeholders and handled according to the pre-agreed rules of engagement.
Is red team testing disruptive to business operations?
Red team testing is designed to be non-disruptive while remaining realistic. We avoid denial-of-service attacks, destructive payloads, or anything that could cause outages or data loss. However, if your security operations team detects our activity and initiates incident response (which is exactly what should happen), this may require time and resources to investigate. We coordinate closely with leadership to manage any potential business impact.
Do we need red team testing if we already do annual penetration testing?
Red team testing and penetration testing serve different purposes. Penetration testing validates that your technical controls are configured correctly and that known vulnerabilities are patched. Red team testing validates that your security operations can detect, respond to, and contain sophisticated multi-stage attacks. Most mature security programmes include both: regular penetration testing to maintain technical security hygiene, and periodic red team assessments to test detection and response capabilities.
How much does red team testing cost?
Red team engagements are significantly more expensive than standard penetration testing because they require more time, expertise, and scope. Costs vary based on engagement duration, objectives, scope, and complexity. A typical red team assessment ranges from several weeks of effort to several months for complex organisations. Contact us for a detailed proposal based on your specific objectives and environment.
Ready to Test Your Security Operations?
Red team testing is the most realistic way to validate whether your security programme can actually detect and stop a determined attacker. If you have invested heavily in security tooling and want assurance it is working, if your board is asking hard questions about your incident response capabilities, or if you simply want to know the truth about your security posture, red teaming provides the answers.
Book a free 30-minute consultation with our team. We will assess your security maturity, discuss potential red team objectives, and explain exactly how an engagement would work for your organisation. Not every company is ready for red teaming, and we will tell you honestly if you would benefit more from penetration testing or vulnerability assessment first.