What We Deliver: Policies That Pass Audits and Actually Work
When you engage Siege Cyber for cyber security policy development, you receive a complete, audit-ready policy framework tailored to your organisation and compliance requirements.
Compliance-Aligned Policy Suite
We develop the complete set of information security policies required for your target framework—ISO 27001, SOC 2, Essential Eight, APRA CPS 234, or a combination. Every policy addresses the specific controls and requirements auditors expect to see, written in language that works for Australian organisations.
Tailored to Your Organisation
We don't just fill in templates with your company name. We interview your team, understand your technology environment, document how you actually operate, and write policies that reflect your reality. Your acceptable use policy references the tools you actually use. Your incident response policy matches your team structure. Your access control policy describes your real provisioning process.
Australian Regulatory Alignment
We incorporate Australian-specific requirements throughout your policy framework. Privacy Act obligations in your data handling policies. OAIC notification procedures in your breach response policy. Essential Eight maturity targets in your patching and access control policies. ACSC guidance where relevant. Your policies work for Australian compliance, not just international standards.
Integration with Vanta and Drata
If you're using Vanta or Drata for compliance automation, we develop policies that integrate seamlessly with the platform while adding the depth and customisation the templates can't provide. We bridge the gap between automation and the human expertise needed to pass audits.
Plain English Documentation
Security policies don't need to sound like legal contracts written by robots. We write in clear, direct language your team can actually understand and follow. Short sentences. Defined terms. Practical examples. Your policies become useful documents, not shelf decorations.
Evidence Package for Auditors
Properly formatted, version-controlled policy documentation ready for ISO 27001 certification audits, SOC 2 assessments, or customer security reviews. We include approval records, review schedules, and the supporting evidence auditors expect to see.
Our Cyber Security Policy Development Process
Step 1: Requirements Analysis and Scoping
We start by understanding your compliance objectives, existing documentation, and organisational context. What framework are you pursuing? What policies already exist? What's your team size and structure? What technology do you use? This shapes the scope and ensures we're writing policies you can actually implement.
Step 2: Gap Analysis Against Framework Requirements
We map your current state against the policy requirements for your target framework. ISO 27001 requires policies for all 93 Annex A controls. SOC 2 Trust Services Criteria need supporting documentation. Essential Eight requires policies for each mitigation strategy. We identify exactly what needs to be developed or updated.
Step 3: Policy Framework Design
We design your complete policy architecture. Which policies will be standalone documents versus integrated into broader governance frameworks? How do policies reference each other? What approval and review cycles make sense for your organisation? We build a structure that's comprehensive but manageable.
Step 4: Stakeholder Interviews and Information Gathering
We interview key stakeholders across your organisation to understand actual processes and practices. How does your dev team actually manage access to production? What's your real patching cadence? How do you currently handle incidents? We document reality, not aspirations, then build policies around improving that reality.
Step 5: Policy Drafting and Review
We write your complete policy suite, policy by policy. Each document goes through internal review, then we share drafts with you for feedback. We iterate based on your input, ensuring every policy accurately reflects your organisation and satisfies framework requirements.
Step 6: Finalisation and Approval Preparation
We deliver final policy documents formatted for approval, version control, and audit submission. We help you establish approval workflows, document policy ownership, and set up review schedules for ongoing maintenance. Everything auditors expect to see is in place.
Step 7: Ongoing Policy Maintenance (Optional)
Policies aren't write-once documents. As your organisation grows, technology changes, and frameworks evolve, policies need updates. Many clients engage our vCISO service to maintain policy frameworks over time, ensuring continuous compliance and audit readiness.
Who Cyber Security Policy Development Is For
Organisations Pursuing ISO 27001 Certification
ISO 27001 requires comprehensive policy documentation covering all implemented controls from Annex A. Auditors expect to see not just templates, but policies that demonstrably reflect your ISMS. We develop the complete ISO 27001 policy suite aligned with the 2022 standard and tailored to your organisation's scope and controls.
Businesses Preparing for SOC 2 Audits
SOC 2 examinations require documented security policies supporting the Trust Services Criteria. Your auditor will assess whether policies exist, are comprehensive, and are actually followed. We develop SOC 2-aligned policies that satisfy auditor requirements and provide the governance foundation your audit needs.
Companies Implementing Essential Eight
The Essential Eight framework requires supporting policies for each mitigation strategy. Application control policies. Patch management policies. MFA policies. Administrative privilege restrictions. We develop Essential Eight-aligned policies that document your implementation and satisfy ACSC guidance and government contract requirements.
Vanta and Drata Users Seeking Certification
You've implemented Vanta or Drata for compliance automation and used their policy templates as a starting point. Now you need expert review and customisation to ensure policies actually match your operations and will pass auditor scrutiny. We're official partners of both platforms and specialise in bridging the gap between automation and certification readiness.
SaaS Companies Responding to Customer Security Questionnaires
Your enterprise customers are sending security questionnaires asking about your information security policies. Do you have an acceptable use policy? Data classification policy? Incident response policy? Third-party risk management policy? We develop the policy framework that lets you answer "yes" with confidence and provide documentation when requested.
Growing Organisations Establishing Security Governance
You've reached the stage where informal security practices aren't enough. You need documented security governance. We help growing Australian SMBs establish proper policy frameworks without the overhead of enterprise-scale documentation programs.
APRA-Regulated Financial Institutions
APRA CPS 234 requires documented information security policies addressing specific risk management requirements. We develop policy frameworks that satisfy APRA expectations while integrating with broader ISO 27001 or industry security standards.

Why Work with Siege Cyber for Policy Development
Official Vanta and Drata Partners
We're official partners of both leading compliance automation platforms. We understand how their policy templates work, where they add value, and where human expertise is essential. If you're using either platform, we'll enhance their foundation with customisation, Australian compliance alignment, and the depth needed to pass certification audits.
Australian Compliance Expertise
We develop policies for Australian organisations, incorporating Privacy Act requirements, OAIC guidance, ACSC Essential Eight standards, APRA CPS 234 for financial services, and other Australian regulatory context. Your policies work for Australian compliance, not just international frameworks translated poorly.
Policies That Reflect Actual Practice
Generic templates describe idealised security programs that don't exist in real SMBs. We document how you actually operate, identify gaps between current practice and compliance requirements, and write policies that bridge that gap realistically. The result is policies your team can follow and auditors will believe.
Experience Across Multiple Frameworks
Many Australian businesses need to satisfy multiple compliance requirements simultaneously—ISO 27001, SOC 2, Essential Eight, Privacy Act obligations. We design integrated policy frameworks that address multiple standards efficiently, avoiding duplication and contradiction.
Technical Depth with Business Context
Our team includes penetration testers, security engineers, and compliance specialists who understand both the technical controls policies need to reference and the business context they operate within. We write policies that are technically accurate and operationally feasible.
Fixed Pricing for Policy Development
After scoping your requirements, we provide fixed-price proposals for developing your complete policy framework. You'll know exactly what the investment is before committing. No hourly billing surprises, no scope creep.
Frequently Asked Questions
How many policies do we need for ISO 27001 certification?
ISO 27001:2022 includes 93 controls across four domains. Most organisations implement 40-60 of these controls depending on their risk assessment and scope. Each implemented control requires supporting documentation, which may be standalone policies, integrated procedures, or references to broader governance documents. We typically develop 15-25 core policy documents for a complete ISO 27001 ISMS, structured to avoid duplication while satisfying all control requirements.
Can we use the policy templates from Vanta or Drata?
Vanta and Drata provide excellent policy templates as a starting point. However, auditors expect policies tailored to your organisation, not generic templates with company names filled in. We work with Vanta and Drata users to review, customise, and enhance platform-generated policies, adding the depth, Australian compliance alignment, and organisational specificity needed to pass certification audits.
How long does it take to develop a complete policy framework?
A full ISO 27001 or SOC 2 policy suite typically takes 4-6 weeks from initial scoping through final delivery. Timeline depends on organisational complexity, how much existing documentation we're building on, and stakeholder availability for interviews and reviews. We provide a detailed timeline after the scoping phase.
Who needs to approve our security policies?
ISO 27001 requires management approval of the ISMS policy and related security documentation. Best practice is executive or board-level approval for high-level governance policies, with appropriate management approval for operational and technical policies. We help you establish appropriate approval workflows and document approval evidence for auditors.
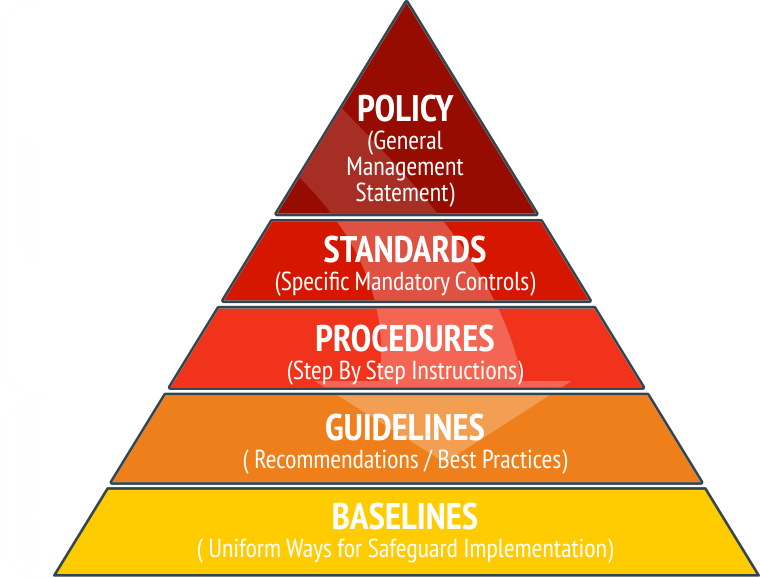
What's the difference between policies, procedures, and standards?
Policies are high-level statements of intent and requirements (what must be done). Procedures are detailed instructions for implementing policies (how to do it). Standards define specific technical requirements (configurations, baselines). A comprehensive security governance framework includes all three. We help you determine the right balance and structure for your organisation.
How often do policies need to be reviewed and updated?
ISO 27001 requires at least annual policy review. In practice, policies should be reviewed when significant changes occur: new systems, regulatory updates, organisational restructuring, or incidents revealing policy gaps. We recommend annual reviews as a baseline with trigger-based reviews for major changes.
Do you provide policy templates we can customise ourselves?
Our service is developing customised policies for your organisation, not providing templates for self-service. Template approaches often fail audits because they don't reflect actual practices. We interview your team, document your environment, and write policies specific to your organisation. The result is audit-ready documentation, not homework for your team.
Will these policies satisfy our Australian regulatory requirements?
Yes. We incorporate Australian-specific requirements throughout policy development: Privacy Act obligations, OAIC notification procedures, ACSC Essential Eight guidance, APRA CPS 234 requirements for financial services, and other Australian regulatory context relevant to your industry and compliance objectives.
Get Your Security Policies Right the First Time
Security policies aren't about ticking compliance boxes. They're the foundation of your security governance, the documentation that proves you take security seriously, and the framework that guides your team's decisions.
Siege Cyber has developed security policy frameworks for Australian SaaS companies, financial services firms, healthcare providers, and SMBs across every sector. We've helped organisations achieve ISO 27001 certification, pass SOC 2 audits, implement Essential Eight, and respond confidently to customer security requirements.
Book a free consultation to discuss your policy development needs. We'll review your compliance objectives, assess what documentation you need, and provide a clear proposal with timelines and fixed pricing. No obligation, no pressure, just honest advice from people who've written hundreds of security policies for Australian organisations.